The definitive guide to who shapes cyber policy in Whitehall, and how to work with them.
Continue reading

The definitive guide to who shapes cyber policy in Whitehall, and how to work with them.
Continue reading
This article traces the emergence of Techstars within the broader history of startup accelerators, examining its strategic differences from Y Combinator, its influence on regional and vertical innovation models, and its role as an institutional entrepreneur in shaping the global accelerator movement. It analyses the evolution from incubators to modern accelerators and critically reflects on Techstars’ legacy in ecosystem building and innovation finance.
Continue reading
Modern Koan from Dune of “Fear Is the Mind-Killer” is not a Zen story, nor is it a koan in the traditional sense. There’s no paradox or puzzle to unravel. But it carries the same contemplative weight. Spoken by Paul Atreides as part of the Bene Gesserit litany, it is a mantra about fear, presence, and the self that remains. Like a koan, it doesn’t resolve the moment; it holds us within it.
Continue reading
This article explores Dante’s Inferno as a structured moral and theological descent, examining the logic behind each of the nine circles of Hell. From lust and gluttony to fraud and treachery, each level reveals how Dante views sin not just as misdeed but as a deformation of the soul and will.
Continue reading
An extensive guide mapping the networks, policy engines, commercial power bases, and future-shapers of British cybersecurity.
Continue reading
Ah, Windows Updates, the perennial thorn in the side of PC users everywhere. Promised as the silent guardians of stability and security, they’ve instead become a source of frustration, disruption, and the occasional catastrophic system crash. Whether it’s an update that bricks your machine or one that installs itself at the worst possible time, Windows Updates have earned their reputation for being, well, bollocks.
Continue reading
Cyber Tzar is a SaaS platform providing advanced cyber risk quantification for enterprise supply chains. It delivers cyber risk scoring, benchmarking, and compliance assessment through big data analytics, AI, and proprietary IP. Its “credit score for cyber” approach supports better risk visibility for insurers, CISOs, and supply chain managers. Cyber Tzar is revenue-generating, scaling through strategic partnerships, and aligned with DORA, ISO 27001, and other regulatory frameworks. Here’s an example “innovation Canvas” for Cyber Tzar.
Continue reading
Innovation is often portrayed as spontaneous and unpredictable. But behind every meaningful breakthrough lies a structured process. Whether you’re launching a new product, transforming a service, or reimagining your organisation’s direction, clarity and rigour are critical.
Continue reading
Influencing senior leaders in cybersecurity and technology is no small task, especially in the UK, where credibility, networks, and standards carry immense weight. Whether you’re a startup founder, a scale-up CISO, or a policy influencer, knowing where the key conversations happen (and who shapes them) can make the difference between being heard and being ignored.
Continue reading
Exactly sixteen years on from my 2009 article on the UK’s economic imbalance, I reflect on how services continue to dominate GDP, while manufacturing still punches above its weight in R&D. I was right about the R&D gap, but missed the rise of intangible capital and startup-led innovation. Cybersecurity emerged as both a strategic asset and an innovation driver. Government efforts have been patchy, and real balance remains elusive. The future lies in resilience, not symmetry.
Continue reading
The Zen Koan of the Two Monks and the Woman is a well-known story that invites reflection on the nature of judgment, letting go, and the burdens we choose to carry.
Continue reading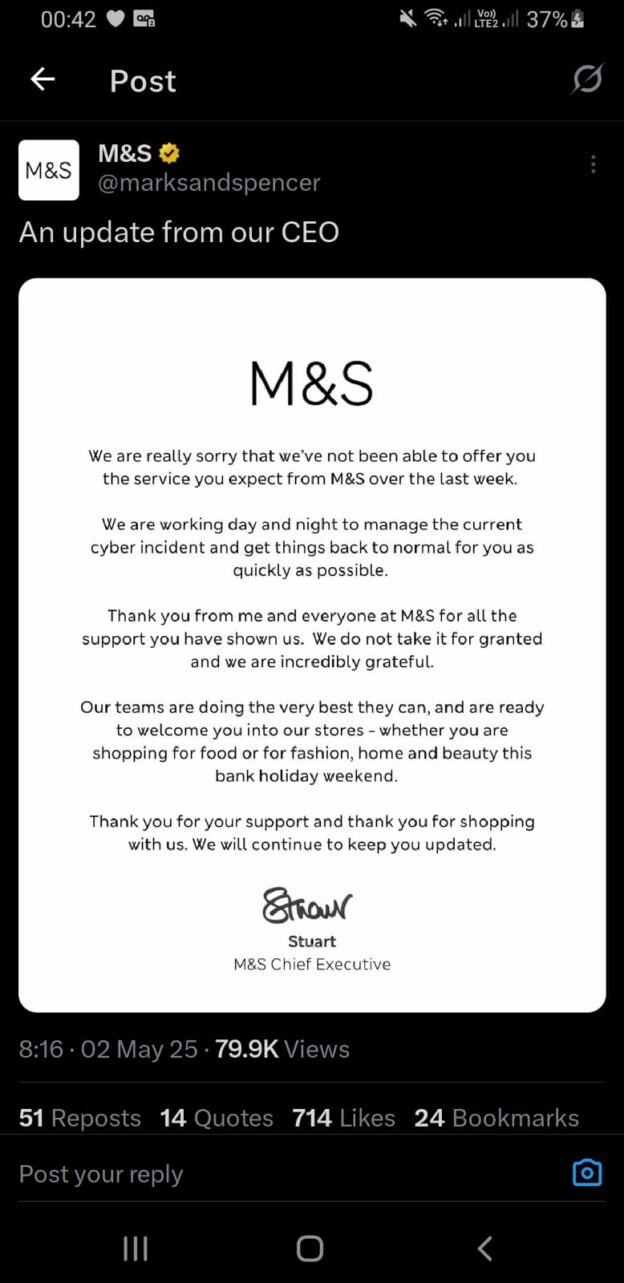
A blunt critique of organisations that claim to be resilient but have never stress-tested their systems, rehearsed recovery under pressure, or practised failure in any meaningful way. The article challenges boardroom bravado and highlights the psychological and operational consequences of untested confidence, arguing that true resilience is earned through discomfort, not declared in policy.
Continue reading
Two senior leaders, Sir Charlie Mayfield, former John Lewis chairman, and Sir Dan Moynihan, CEO of the Harris Federation, joined BBC Radio 4’s Today Programme on 1 May 2025 to discuss the impact of recent cyber attacks on Marks & Spencer, the Co-op, and UK schools. Their stories offer rare insight into how institutions respond to major breaches and what it really takes to recover.
Continue reading
Rump steak can be deliciously tender when treated right. This guide covers how to prep, season, sear, and rest your steak for maximum flavour and minimal chew.
Continue reading
Blogging is often touted as a straightforward path to online fame, fortune, and influence. The internet is awash with advice claiming that with a few simple steps, anyone can turn their blog into a passive income machine or a platform for global recognition. But behind the polished success stories lies a lot of misinformation, unrealistic expectations, and outright bollocks.
Continue reading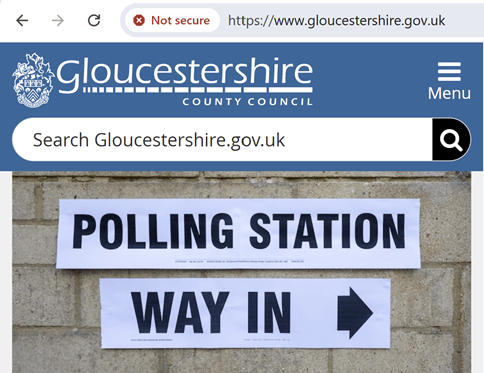
While applying for a parking permit, I discovered an expired SSL certificate on a council website, highlighting how small oversights in public services can expose broader cybersecurity risks. This real-world example shows why organisations must take indirect supply chain risk seriously, particularly in regions critical to national security.
Continue reading