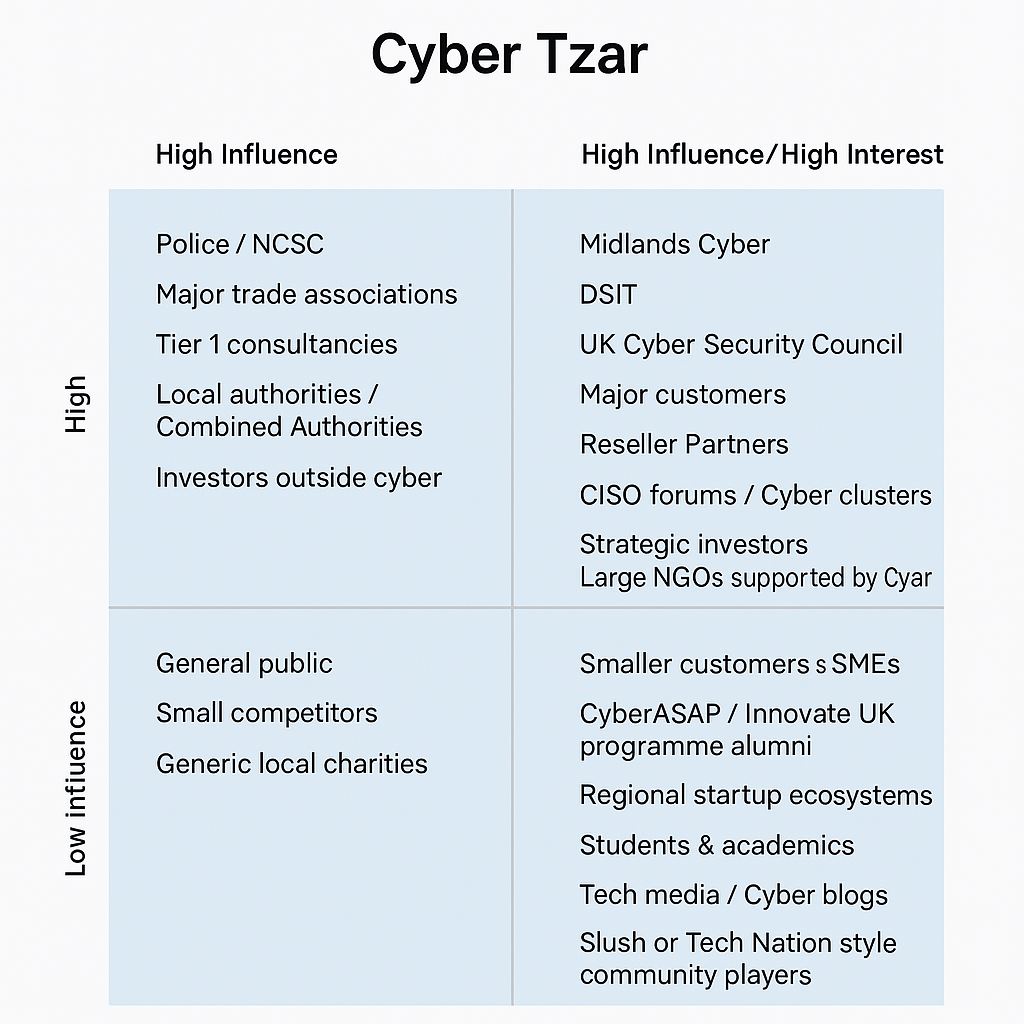
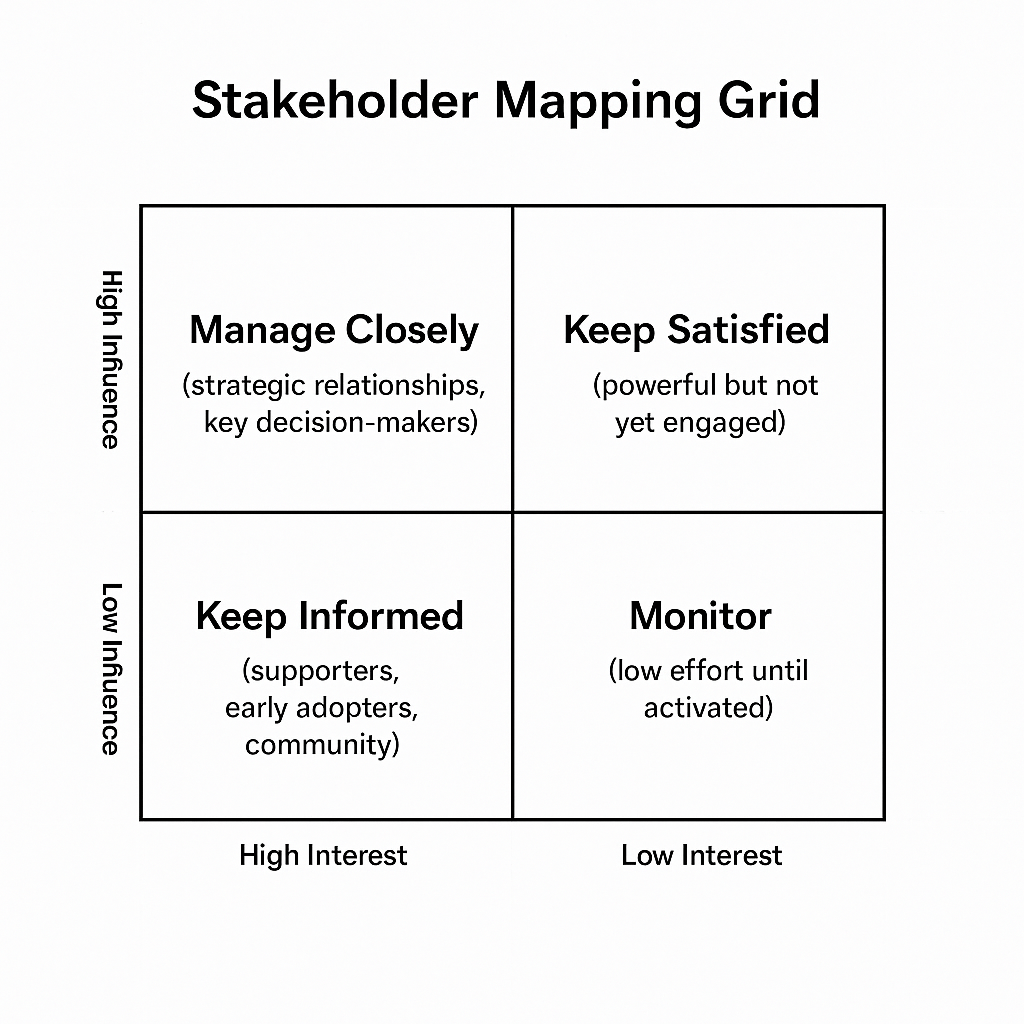
Understanding your stakeholder landscape is key to scaling effectively, especially in cybersecurity, where trust, standards, and adoption often hinge on who’s in the room. This article explores how Cyber Tzar, a cybersecurity scale-up specialising in supply chain risk and cyber risk scoring, applies the Stakeholder Mapping Grid to guide its strategic engagement.
Continue reading