This article introduces the Virtuous Triangle as a strategic framework for understanding cyber risk through the combined lenses of vulnerability assessment, threat intelligence, and contextual risk analysis. It argues that meaningful risk assessment only emerges when these components are integrated and automated at scale. Drawing on decades of experience, the piece reflects on the limitations of standalone data and the necessity of systems thinking in cybersecurity.
Risk is a moving target. We like to imagine it as a fixed object, a metric, a number, a score, something that can be benchmarked, compared, and improved. But the truth is: risk is situational. It’s contextual. It’s shaped by exposure, adversary intent, and the structural weaknesses we inherit, overlook, or create.
After over thirty years in technology, from national infrastructure to early-stage startups, I’ve come to view cyber risk not as a function of controls or compliance, but as something more dynamic: a tension between what you know, what you don’t, and what the adversary does.
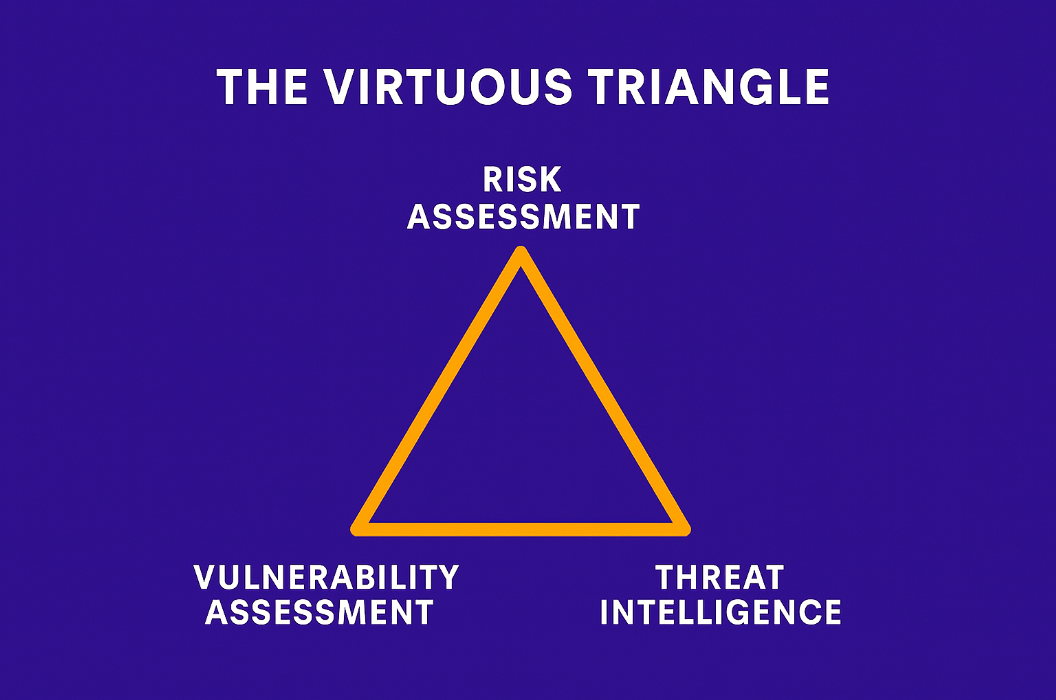
This thinking forms the basis of what I call the Virtuous Triangle of automated risk assessment at scale, a mental model we’ve operationalised at Cyber Tzar, but one I believe applies far more broadly than any one platform.
Three Lenses, One Objective
Risk, in its most useful sense, is a synthesis. You need visibility, awareness, and judgment. Or in more practical terms:
Vulnerabilities, threats, and impact.
- Vulnerability Assessments tell you what’s exposed, misconfigured, outdated, or forgotten.
- Threat Intelligence tells you what’s being exploited right now, by whom, and how.
- Risk Assessment ties it together, offering prioritisation rooted in consequences.
Each one on its own is useful. But together, and only together, they become more than the sum of their parts. A virtuous triangle, not just a technical one.
Vulnerability: Knowing What’s Broken
Every system drifts. Configurations decay. Dependencies rot. Once secure things now pose a threat, not because they changed, but because the world around them did.
Vulnerability scanning is the archaeology of digital infrastructure. It surfaces the buried, the broken, the legacy, the left-behind. But the raw signal alone doesn’t give us meaning. It gives us surface area. It tells us where the problem might be, not whether it matters.
Threat Intelligence: Knowing What’s Coming
The second lens, threat intelligence, cuts across time. It introduces urgency. We no longer ask “What’s wrong?” but “What’s being actively exploited, and does it relate to me?”
This is where patterns emerge. Malware families, phishing campaigns, exploit kits, deep fakes, social engineering playbooks, all swirling in the digital ether, reshaping the risk landscape not in theory, but in real time.
The art lies in connecting this external momentum with your internal posture. Because risk isn’t just about being vulnerable, it’s about being vulnerable to things that matter.
Risk Assessment: Knowing What to Do
The final point in the triangle is risk itself. True risk. Not just likelihood × impact, but context × relevance.
Risk is about stories. About the consequence. It’s the difference between a misconfigured DMARC record being a minor hygiene issue or the reason you just lost £1.2m to a CEO fraud attack.
Good risk assessments don’t just list problems. They prioritise action. They say: this is the issue, this is why it matters, and here’s what you need to do. Clarity over chaos. Strategy over checklist.
Why It’s a Virtue
I call it the Virtuous Triangle, not purely to sound clever, but to emphasise the feedback loop. When done right, each part improves the others. But not a circle, because this model has the strength of the triangle supporting it.
- Vulnerability data becomes more relevant with real threat intel.
- Threat intel becomes more actionable with exposure context.
- Risk assessments become more accurate with both.
This is where automation plays a vital role. Not to replace the human, but to scale the insight.
And when you do that, across 130,000+ organisations (as we’ve done at Cyber Tzar), you begin to see patterns emerge, systemic weaknesses, shared blind spots, regional trends, and industry-specific gaps. It’s less about any one breach and more about understanding the system as a whole.
Final Reflections
The world is noisy. The cyber world doubly so. Every vendor promises clarity; every dashboard promises insight. But too often we’re left drowning in data and starving for meaning.
The Virtuous Triangle isn’t a product. It’s a framing. A way to cut through the noise and anchor ourselves to what actually matters.
In the end, cyber risk is a question of alignment: between what you know and what you do. And if we can automate the right questions, with the right inputs, we stand a chance of making the answers count.